History Of VPNs
Have you ever wondered how VPNs came into existence and evolved to become an integral part of our digital lives? In this article, we will take a captivating journey through the history of VPNs, shedding light on their origins, advancements, and the impact they have had on our online security and privacy. Whether you are a newbie or a tech-savvy individual, this exploration of the past will give you a comprehensive understanding of how VPN technology has shaped the way we navigate the virtual realm. So, fasten your seatbelts and get ready to embark on a fascinating historical excursion into the world of VPNs.
History of VPNs
Virtual Private Networks (VPNs) have come a long way since their inception, evolving from a niche technology to become an integral part of our digital lives. This article delves into the history of VPNs, tracing their early development, the emergence of tunneling protocols, the commercialization of VPNs, advancements in encryption, increasing popularity and adoption, as well as the evolution of VPN technology.
Early Development of VPNs
Origins of Virtual Private Networks
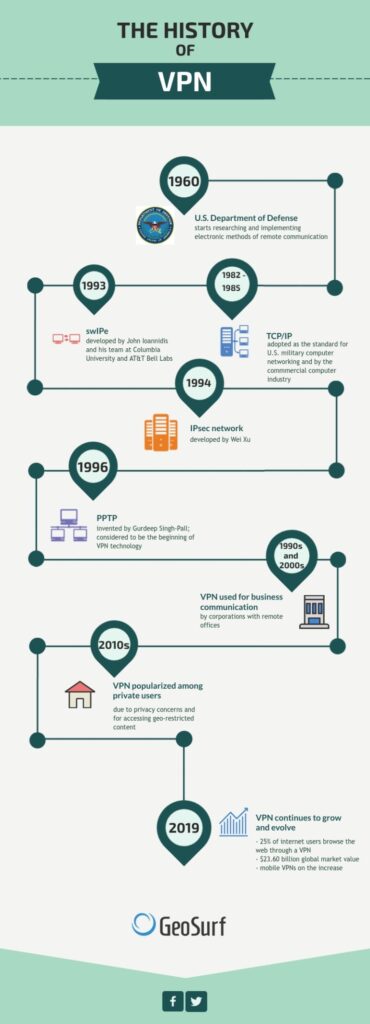
The concept of a Virtual Private Network can be traced back to the 1970s when researchers started exploring ways to securely connect remote computer networks. The primary objective was to create a private network connection over a public network, ensuring confidentiality and data integrity.
Development of Wide Area Networks
The development of Wide Area Networks (WANs) in the 1980s laid the foundation for the implementation of VPNs. WANs enabled the connection of geographically dispersed computer networks, and VPNs leveraged this infrastructure to create secure connections over long distances.
Integration of Encryption Techniques
Encryption played a crucial role in the early development of VPNs. Researchers experimented with different encryption techniques to protect data transmitted over public networks. The integration of encryption allowed for the establishment of secure communication channels, ensuring the privacy and security of sensitive information.
Emergence of Tunneling Protocols
Introduction of PPTP
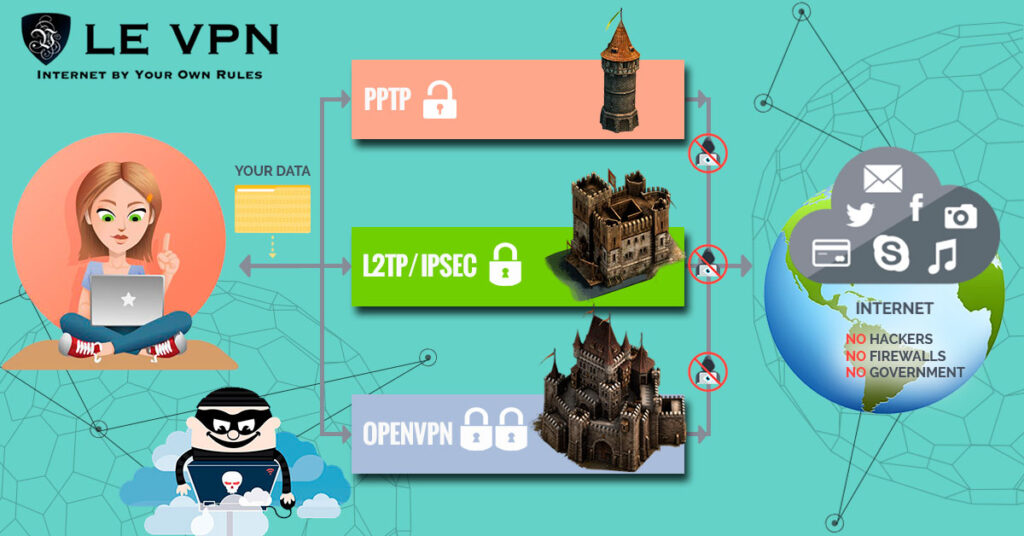
In the early 1990s, Microsoft introduced the Point-to-Point Tunneling Protocol (PPTP), which revolutionized the concept of VPNs. PPTP allowed users to establish secure connections by encapsulating data packets within an IP tunnel. This protocol became widely adopted due to its compatibility with various operating systems.
Invention of L2F and L2TP
Following the introduction of PPTP, the Layer 2 Forwarding (L2F) protocol was developed by Cisco Systems. L2F provided enhanced security features and improved interoperability. Later, L2F was merged with another protocol called Layer 2 Tunneling Protocol (L2TP), resulting in a more robust and widely supported tunneling protocol.
Development of IPsec
The IPsec (Internet Protocol Security) protocol emerged as a reliable solution for securing VPN connections in the late 1990s. IPsec offered end-to-end encryption and authentication, ensuring secure communication between network endpoints. Its widespread adoption significantly enhanced the security and reliability of VPNs.
Commercialization of VPNs
VPN Service Providers
As the demand for secure remote connectivity increased, numerous companies recognized the business potential of providing VPN services. VPN service providers emerged, offering individuals and organizations the ability to establish secure connections without the need for extensive technical expertise.
VPN Hardware Solutions
Apart from VPN service providers, hardware vendors also played a crucial role in the commercialization of VPNs. They developed dedicated VPN hardware solutions, such as routers and firewalls, which integrated VPN functionality into the network infrastructure. These solutions simplified the deployment and management of VPNs for organizations.
Introduction of SSL VPNs
Another significant development in the commercialization of VPNs was the introduction of Secure Sockets Layer (SSL) VPNs. SSL VPNs provided secure remote access to web applications without the need for installing dedicated client software. This simplified the user experience and expanded the range of devices that could securely connect to VPNs.
Advancements in Encryption
DES and 3DES
The Data Encryption Standard (DES) was one of the earliest encryption algorithms used in VPN implementation. However, with advancements in computing power, the security of DES was compromised, leading to the development of Triple DES (3DES). 3DES offered stronger encryption, providing improved protection for VPN communication.
Introduction of AES
The Advanced Encryption Standard (AES) replaced DES and 3DES as the standard encryption algorithm for VPNs. AES offered a higher level of security while maintaining efficient performance. Its widespread adoption by VPN providers ensured robust encryption for data transmitted over VPN connections.
Key Exchange Protocols
In addition to encryption algorithms, key exchange protocols played a vital role in enhancing VPN security. Protocols like Diffie-Hellman and Internet Key Exchange (IKE) facilitated the secure exchange of encryption keys between VPN clients and servers, ensuring confidential communication.
Increasing Popularity and Adoption
VPN Usage in Business Environment
As the internet became an integral part of business operations, organizations widely adopted VPN technology to secure their internal network communications. VPNs enabled employees to securely access sensitive data and connect to remote office networks from anywhere in the world, significantly improving productivity and flexibility.
Remote Access VPNs for Telecommuting
The rise of remote work and telecommuting further drove the popularity of VPNs. Remote Access VPNs allowed employees to connect securely to their organization’s network, accessing resources as if they were physically present in the office. This enabled seamless collaboration and eliminated the need for dedicated leased lines.
Privacy and Anonymity Concerns
In an era of increasing online surveillance and censorship, individuals also turned to VPNs to protect their online privacy and bypass restrictions. VPNs provided a way to mask their IP addresses, encrypt their internet traffic, and access geo-restricted content, becoming an essential tool for internet users concerned about their privacy and freedom.
Evolution of VPN Technology
Multi-Protocol Label Switching
Multi-Protocol Label Switching (MPLS) emerged as a new approach to VPN implementation in the late 1990s. MPLS allowed for the creation of virtual private networks within service provider networks, providing enhanced performance, scalability, and traffic engineering capabilities.
Mobile VPNs
With the widespread adoption of mobile devices, the need for secure connectivity on the go became evident. Mobile VPNs were developed to secure communication between mobile devices and corporate networks, enabling employees to access company resources securely while on the move.
Next-Generation Firewalls with VPN Capabilities
As cybersecurity threats evolved, so did VPN technology. Next-generation firewalls integrated VPN capabilities, offering organizations a holistic approach to network security. These firewalls provided advanced threat prevention, deep packet inspection, and VPN functionality in a single device, simplifying network management and improving overall security posture.
Future of VPN Technology
Enhanced Privacy Features
As privacy concerns continue to grow, VPNs are likely to incorporate enhanced privacy features. These may include features like secure DNS resolution, advanced leak protection, and built-in ad blockers, offering users comprehensive privacy and security when connected to a VPN.
Integration with IoT Devices
The proliferation of Internet of Things (IoT) devices brings new challenges for security and privacy. VPN technology is expected to integrate with IoT devices, ensuring secure and encrypted communication between these devices and the internet. This integration will protect sensitive information and mitigate the risk of unauthorized access.
Advancements in Speed and Performance
In the future, VPN technology is likely to witness significant advancements in terms of speed and performance. VPN providers will invest in optimizing their networks, leveraging technologies like faster encryption algorithms, improved protocols, and better infrastructure, ensuring minimal impact on internet speed while using a VPN.
In conclusion, the history of VPNs showcases the remarkable evolution of this technology from its early development to its commercialization and widespread adoption. With advancements in encryption, the increasing popularity in various domains, and the ever-evolving VPN technology, VPNs are poised to play a crucial role in ensuring privacy, security, and seamless connectivity in our interconnected world.