Choosing the Right VPN Protocol For Your Needs
In this article, we’ll be discussing VPN protocols – the backbone of any VPN service. Whether you’re a beginner just getting started with VPNs or an advanced user looking to expand your knowledge, understanding VPN protocols is essential. We’ll explore the history of these protocols and their application in a range of scenarios, from ensuring secure gaming experiences to protecting corporate data. By the end, you’ll have a solid grasp on VPN protocols and their significance in the world of virtual private networks. So, let’s jump right in and explore the world of VPN protocols!
1. Introduction to VPN Protocols
1.1 What is a VPN?
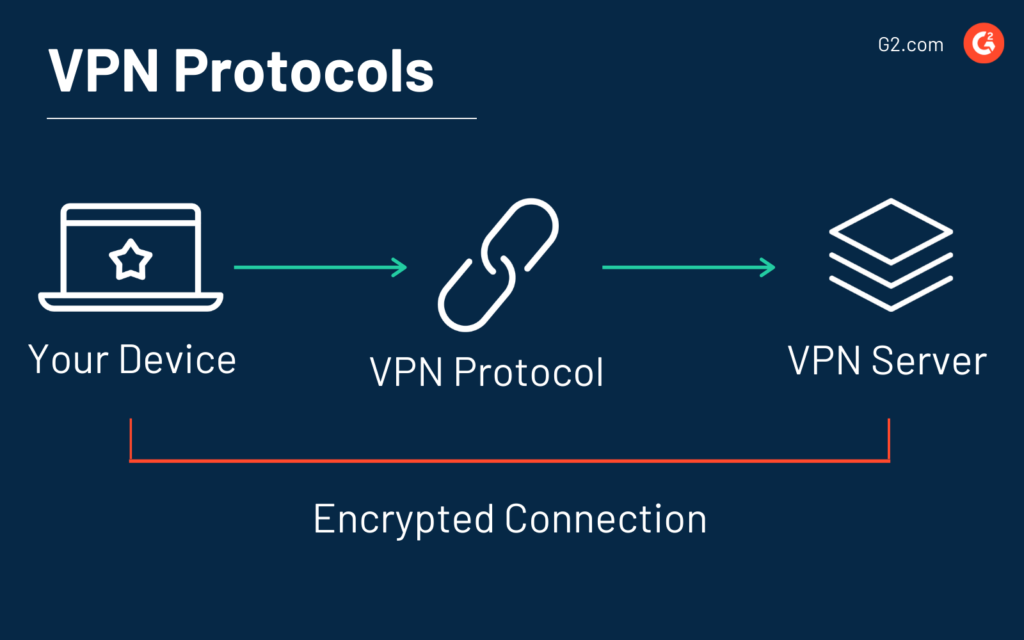
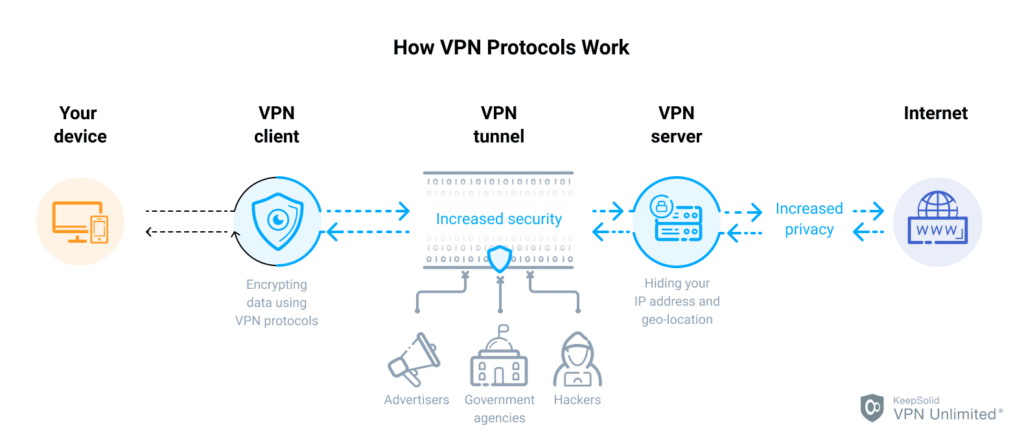
A VPN, or Virtual Private Network, is a technology that allows you to establish a secure and encrypted connection over a public network, such as the internet. It enables you to create a private network that extends across the internet, connecting your device or network to another network or server located elsewhere. This creates a virtual tunnel through which your data is transmitted, ensuring privacy, confidentiality, and security.
1.2 What is a VPN Protocol?
A VPN protocol refers to the set of rules and procedures used to govern the establishment, maintenance, and security of the VPN connection. It determines how data is encapsulated, encrypted, and transmitted between your device and the VPN server. VPN protocols vary in terms of their security features, speed, compatibility, and ease of use.
1.3 Importance of VPN Protocols
VPN protocols play a crucial role in ensuring the effectiveness and security of your VPN connection. They determine the level of encryption, authentication methods, and other security features that protect your data from unauthorized access. With the increasing importance of online privacy and security, choosing a suitable VPN protocol is essential to safeguard your sensitive information and maintain your anonymity while browsing the internet.
2. Common VPN Protocols
2.1 PPTP (Point-to-Point Tunneling Protocol)
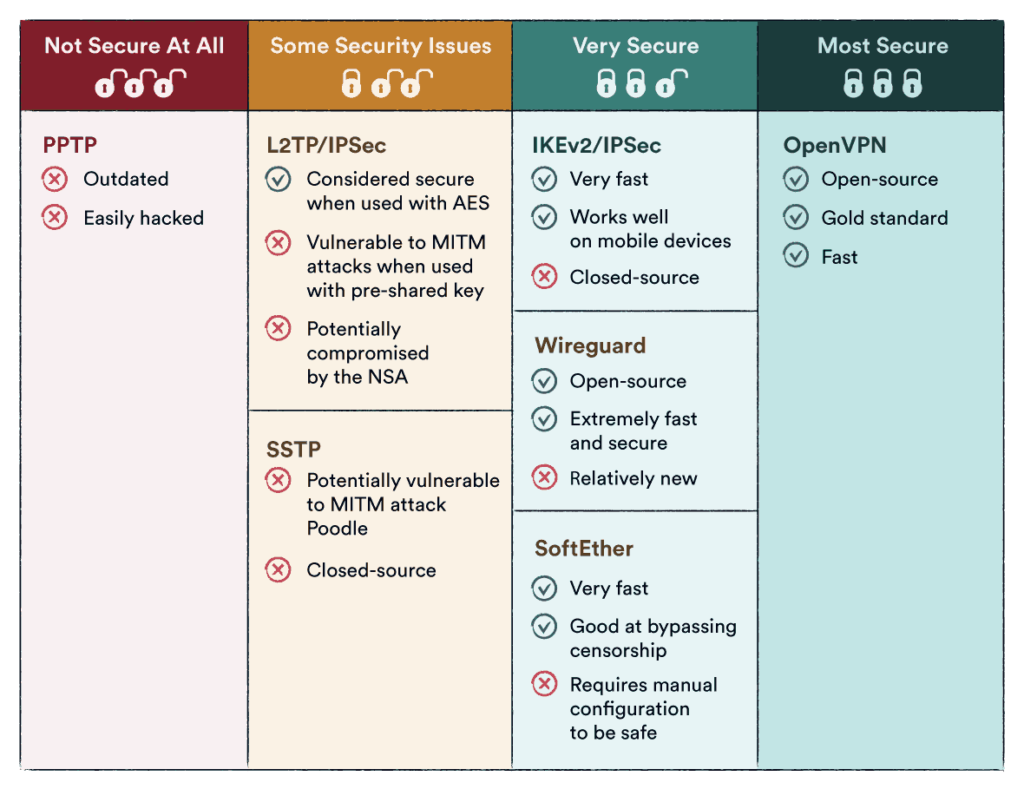
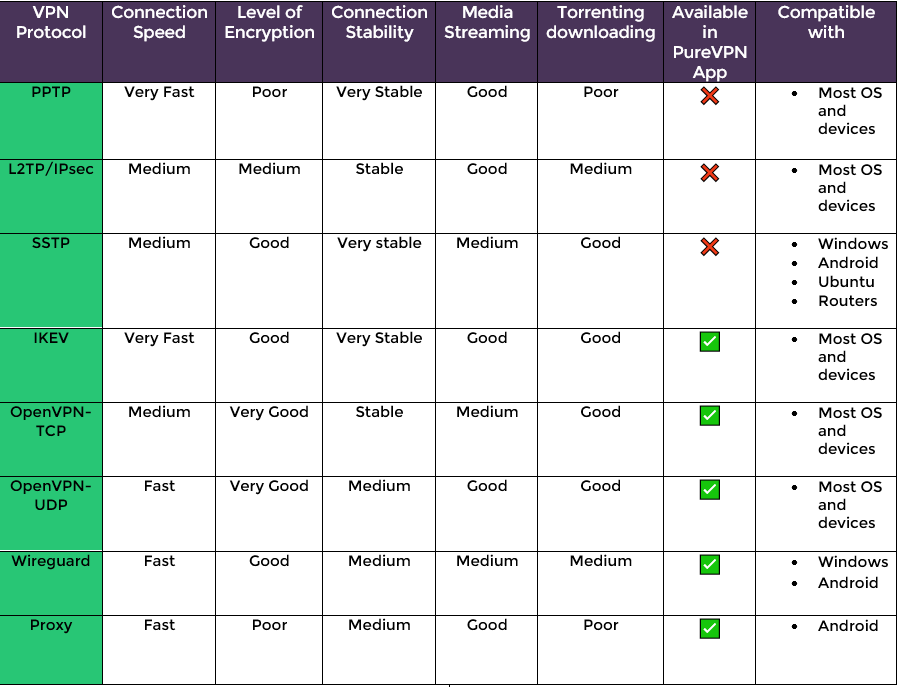
PPTP is one of the oldest and most widely used VPN protocols. It is supported by most operating systems and devices, making it highly compatible. However, PPTP has known security weaknesses and is considered less secure compared to other protocols. It uses weak encryption algorithms and lacks advanced security features, making it vulnerable to attacks. While it may offer faster speeds, it is not recommended for users who prioritize privacy and security.
2.2 L2TP (Layer 2 Tunneling Protocol)
L2TP is often used in conjunction with IPsec (Internet Protocol Security) to provide a more secure VPN connection. It offers stronger encryption and authentication mechanisms compared to PPTP. L2TP/IPsec is widely supported on various devices and operating systems. However, due to its double encapsulation and additional protocol overhead, L2TP/IPsec can be slower than other protocols, especially when used over long distances.
2.3 SSTP (Secure Socket Tunneling Protocol)
SSTP is a protocol developed by Microsoft and primarily used on Windows operating systems. It provides a highly secure connection by utilizing the SSL/TLS encryption protocol, making it difficult to intercept or decrypt. SSTP is also known for its ability to bypass firewalls and restrictive networks, as it uses the standard HTTPS port (port 443). However, being predominantly available on Windows platforms, its usage may be limited for users operating on other operating systems.
2.4 OpenVPN
OpenVPN is an open-source VPN protocol that has gained popularity due to its excellent security and flexibility. It uses customizable encryption protocols, including AES (Advanced Encryption Standard), offering robust protection for your data. OpenVPN is supported on multiple platforms, including Windows, macOS, Linux, iOS, and Android. Its open-source nature allows for continuous improvement and auditing, guaranteeing a reliable and secure VPN connection.
2.5 IKEv2 (Internet Key Exchange version 2)
IKEv2 is a protocol often used in combination with IPsec for secure VPN connections. It is known for its fast and stable performance, making it suitable for mobile devices and unstable network connections. IKEv2 offers built-in support for mobility and can seamlessly switch between Wi-Fi and cellular networks without disrupting the connection. This protocol provides strong encryption and authentication, making it a reliable choice for security-conscious users.
3. Comparison of VPN Protocols
3.1 Security
When it comes to security, OpenVPN and IKEv2 are considered to be the most secure VPN protocols. They both offer robust encryption algorithms and advanced security features, such as mutual authentication and perfect forward secrecy. In contrast, PPTP is the least secure protocol, with known vulnerabilities that make it susceptible to eavesdropping and attacks.
3.2 Speed
PPTP generally provides faster speeds compared to other protocols due to its lower encryption overhead. However, advancements in encryption algorithms have optimized the performance of OpenVPN and IKEv2, making them competitive in terms of speed.
3.3 Compatibility
PPTP has the advantage of being widely supported across devices and operating systems. However, it is gradually being phased out in favor of more secure protocols. OpenVPN and IKEv2 offer broader compatibility and are supported on various platforms, including Windows, macOS, Linux, iOS, and Android.
3.4 Ease of Use
PPTP is known for its simplicity and ease of use, making it suitable for beginners. OpenVPN and IKEv2 may require additional software installations or manual configuration, making them slightly more complex for inexperienced users.
3.5 Stability
OpenVPN and IKEv2 generally provide stable connections even on unreliable networks, thanks to their ability to handle network fluctuations and seamlessly switch between Wi-Fi and cellular connections. PPTP, on the other hand, may experience stability issues, especially on congested or high-latency networks.
4. Legacy VPN Protocols
4.1 IPSec
IPsec, also known as Internet Protocol Security, is a widely used protocol suite for securing IP communications. It provides authentication, confidentiality, and integrity for IP packets, ensuring secure data transmission. IPsec can operate in two modes: transport mode (encrypting only the data payload) and tunnel mode (encrypting the entire IP packet). However, IPsec may require manual setup and additional software on certain devices.
4.2 SSL
SSL, or Secure Sockets Layer, is an encryption protocol widely used for securing communication over the internet. It creates a secure connection between a client and a server and is commonly used in web browsers for HTTPS connections. While SSL can be used as a VPN protocol, it is often used in conjunction with other protocols such as L2TP or IKEv2 to establish a secure VPN connection.
4.3 PPTP (Point-to-Point Tunneling Protocol)
As discussed earlier, PPTP is a legacy VPN protocol known for its fast speeds but weak security. While it is still supported by many devices, its usage is diminishing due to security vulnerabilities.
4.4 L2TP (Layer 2 Tunneling Protocol)
L2TP is a legacy protocol often combined with IPsec for secure VPN connections. It provides a secure tunnel for data transmission, but its slower performance and additional protocol overhead have made it less popular compared to newer protocols like OpenVPN and IKEv2.
4.5 SSTP (Secure Socket Tunneling Protocol)
SSTP, developed by Microsoft, is a legacy protocol primarily used on Windows platforms. It utilizes the SSL/TLS encryption protocol to establish a secure VPN connection. While SSTP offers strong security, its limited compatibility with non-Windows operating systems and devices makes it less widely used.
5. Modern VPN Protocols
5.1 OpenVPN
OpenVPN, an open-source VPN protocol, has emerged as a modern and highly secure option. With customizable encryption and authentication mechanisms, it provides strong and reliable security. OpenVPN is widely supported on multiple platforms, making it a popular choice for both individuals and organizations.
5.2 IKEv2 (Internet Key Exchange version 2)
IKEv2, often used in conjunction with IPsec, is a modern VPN protocol known for its fast and stable performance. It offers strong security features, making it suitable for users who prioritize both speed and security. IKEv2 is particularly convenient for mobile devices, as it seamlessly handles network fluctuations.
5.3 WireGuard
WireGuard is a relatively new VPN protocol designed to be faster, easier to set up, and more secure than traditional protocols. It aims to simplify the VPN experience while maintaining robust security. With its lightweight design and efficient codebase, WireGuard offers fast speeds and high performance.
5.4 SoftEther
SoftEther is an open-source VPN protocol that combines the functionality of multiple VPN protocols, including L2TP/IPsec, OpenVPN, and SSTP. It provides a versatile and flexible solution for creating secure VPN connections. SoftEther supports a wide range of operating systems, making it an attractive option for users who need cross-platform compatibility.
6. Security Features in VPN Protocols
6.1 Encryption
Encryption is a crucial aspect of VPN protocols, as it ensures that your data remains confidential and secure during transmission. Strong encryption algorithms, such as AES, are used to encrypt your data, making it unreadable to unauthorized individuals. VPN protocols differ in the level of encryption they offer, with modern protocols like OpenVPN and IKEv2 providing robust encryption mechanisms.
6.2 Authentication
Authentication is the process of verifying the identity of the parties involved in a VPN connection. It ensures that only authorized users can access the VPN and prevents unauthorized access. VPN protocols use various authentication methods, such as username and password, certificates, or two-factor authentication, to verify the identities of both the client and the server.
6.3 Data Integrity
Data integrity ensures that your data remains unaltered and tamper-free during transmission. VPN protocols employ cryptographic hash functions to verify the integrity of transmitted data. This prevents data from being modified or tampered with during transit, ensuring the reliability and trustworthiness of the information being transmitted.
6.4 Perfect Forward Secrecy (PFS)
Perfect Forward Secrecy, or PFS, is a security feature that ensures the privacy of your data even if the encryption key is compromised. It achieves this by generating a unique session key for each VPN session, making it difficult to decrypt previously captured data if the session key is obtained. VPN protocols like OpenVPN and IKEv2 support PFS, providing an additional layer of security.
7. Factors to Consider When Choosing a VPN Protocol
7.1 Privacy and Security Requirements
Different users have different privacy and security requirements. If your primary concern is privacy and security, it is recommended to choose protocols like OpenVPN or IKEv2, which offer strong encryption and advanced security features. If speed is more important to you, protocols like PPTP may be a consideration, although they provide weaker security.
7.2 Speed and Performance Needs
Consider your speed and performance needs when choosing a VPN protocol. PPTP generally offers faster speeds, but if security is a priority, modern protocols like OpenVPN and IKEv2 provide a good balance between speed and security. WireGuard is also known for its fast performance and low latency.
7.3 Device and Operating System Compatibility
Ensure that the VPN protocol you choose is compatible with your device and operating system. PPTP, despite its weaknesses, is widely supported across platforms. OpenVPN and IKEv2 are compatible with multiple operating systems, including Windows, macOS, Linux, iOS, and Android. WireGuard and SoftEther also offer compatibility on various platforms.
7.4 Ease of Configuration
Consider the level of technical expertise required to configure and set up the VPN protocol. PPTP is known for its simplicity and ease of use, making it suitable for beginners. OpenVPN and IKEv2 may require additional software installations or advanced configuration, which may be more suitable for experienced users.
7.5 Geo-blocking and Bypassing Restrictions
If bypassing geo-blocking or accessing restricted content is important to you, choose a protocol that is known for its ability to circumvent such restrictions. OpenVPN and IKEv2 are often effective in bypassing firewalls and restrictive networks, allowing you to access content that may be blocked based on your location.
8. VPN Protocol Specific Applications
8.1 Gaming
Using a VPN can have advantages for gamers, such as reducing latency and protecting against DDoS attacks. VPN protocols like OpenVPN and WireGuard provide low latency and fast connections, making them suitable for online gaming. Additionally, VPNs can be used to access games and content that may be restricted in certain regions.
8.2 Streaming
VPN protocols that provide fast speeds and reliable connections, such as PPTP, OpenVPN, and WireGuard, are ideal for streaming content from platforms like Netflix, Hulu, or BBC iPlayer. By connecting to a VPN server in a different region, you can bypass geo-restrictions and access a wider range of content.
8.3 Corporate Networks
VPN protocols like OpenVPN and IKEv2 are often used in corporate environments to provide secure remote access to corporate networks and resources. These protocols offer strong encryption and authentication, ensuring that sensitive corporate data remains protected while employees work remotely.
8.4 Mobile Devices
For mobile devices, VPN protocols that support seamless handoff between Wi-Fi and cellular connections, such as IKEv2, are highly recommended. These protocols allow for uninterrupted VPN connections, even when switching networks, making them ideal for users on the move.
8.5 Remote Access
VPN protocols that provide secure remote access to networks, such as OpenVPN, IKEv2, and SoftEther, are commonly used for remote working. These protocols offer strong encryption and authentication, allowing employees to access corporate resources securely from remote locations.
9. VPNs and Cybersecurity
9.1 VPN Protocols and Data Protection
VPN protocols play a critical role in ensuring the privacy and security of your data. By encrypting your data and establishing a secure connection, VPN protocols protect your information from being intercepted or accessed by unauthorized individuals. Strong encryption, authentication, and data integrity mechanisms provided by modern protocols like OpenVPN and IKEv2 enhance the overall cybersecurity of your online activities.
9.2 VPNs for Secure Remote Work
As remote work becomes increasingly prevalent, the use of VPNs for secure remote access to corporate networks is essential. VPN protocols like OpenVPN and IKEv2 enable employees to connect to their company’s network securely, ensuring the protection of sensitive data and maintaining the integrity of communications.
9.3 VPNs for Public Wi-Fi Safety
Using public Wi-Fi networks can expose you to various security risks, such as eavesdropping and data theft. VPN protocols establish an encrypted connection between your device and the VPN server, protecting your data from potential threats on public Wi-Fi networks. It is especially important to use secure VPN protocols like OpenVPN or IKEv2 when accessing sensitive information on public Wi-Fi.
9.4 VPNs for Anti-censorship
VPNs are often used to bypass censorship and access restricted content or websites. By connecting to a VPN server located in a different region or country, users can circumvent censorship filters and access content that may otherwise be blocked. VPN protocols that are effective in bypassing censorship, such as OpenVPN, can help promote internet freedom and open access to information.
10. Choosing the Right VPN Protocol for Your Needs
10.1 Assessing Your Requirements
Before choosing a VPN protocol, it is important to assess your specific requirements. Consider factors such as privacy and security needs, speed and performance requirements, compatibility with your devices and operating systems, ease of configuration, and the ability to bypass restrictions or access geo-blocked content. Understanding your specific needs will help guide you in selecting the most suitable VPN protocol.
10.2 Understanding Trade-offs
Different VPN protocols offer varying levels of security, speed, and compatibility. It is important to understand the trade-offs associated with each protocol. For example, while PPTP may provide faster speeds, it sacrifices security. Conversely, protocols like OpenVPN and IKEv2 prioritize security but may require additional software installations or advanced configuration.
10.3 Seeking Expert Advice
If you are unsure about which VPN protocol to choose, seeking expert advice can be beneficial. VPN service providers or cybersecurity professionals can guide you in selecting the most appropriate protocol based on your specific needs. They can provide insights into the strengths and weaknesses of different protocols and help you make an informed decision.
10.4 Testing Different Protocols
Consider testing different VPN protocols to determine which one best suits your needs. Many VPN service providers offer free trials or money-back guarantees that allow you to evaluate the performance, compatibility, and user experience of different protocols. Try using different protocols on different devices and networks to evaluate their strengths and weaknesses in real-world scenarios.
10.5 Considering Future Scalability
When choosing a VPN protocol, remember to consider future scalability. As your needs may change over time, it is important to select a protocol that can accommodate your future requirements. Protocols like OpenVPN and IKEv2, with their broad compatibility and strong security features, provide a good foundation for future scalability and evolving security needs.
In conclusion, VPN protocols play a crucial role in ensuring the security, privacy, and performance of your VPN connection. Understanding the various protocols available and their strengths and weaknesses is essential in choosing the right protocol for your specific needs. Whether you prioritize security, speed, compatibility, or ease of use, there is a VPN protocol that can meet your requirements. By choosing the appropriate protocol and configuring your VPN connection properly, you can enjoy a safe and secure browsing experience while protecting your sensitive information from unauthorized access.